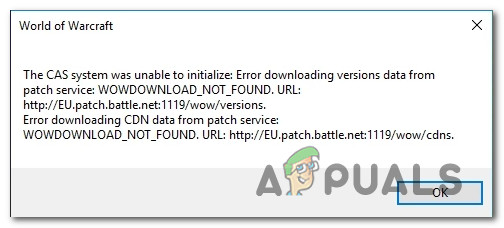
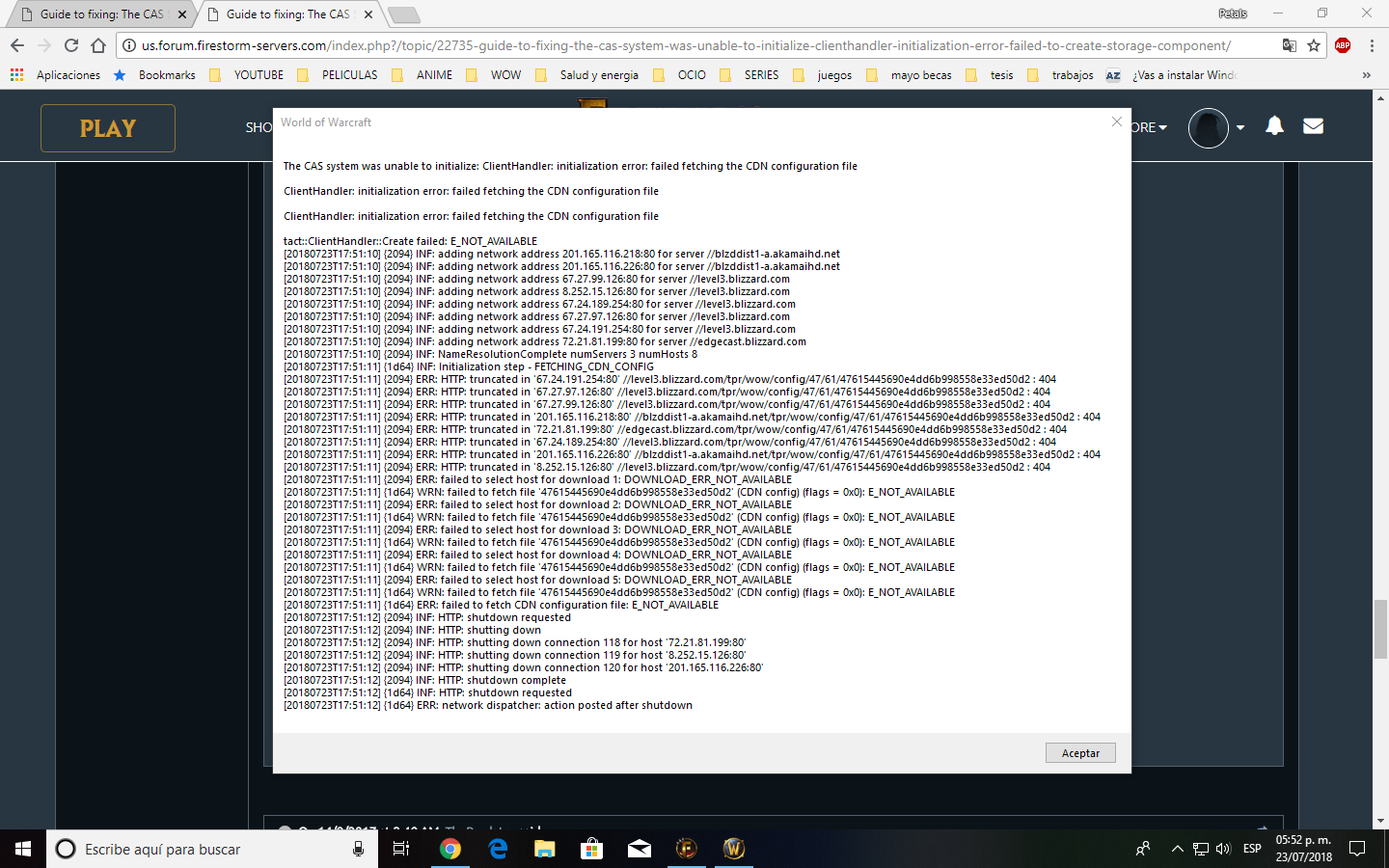
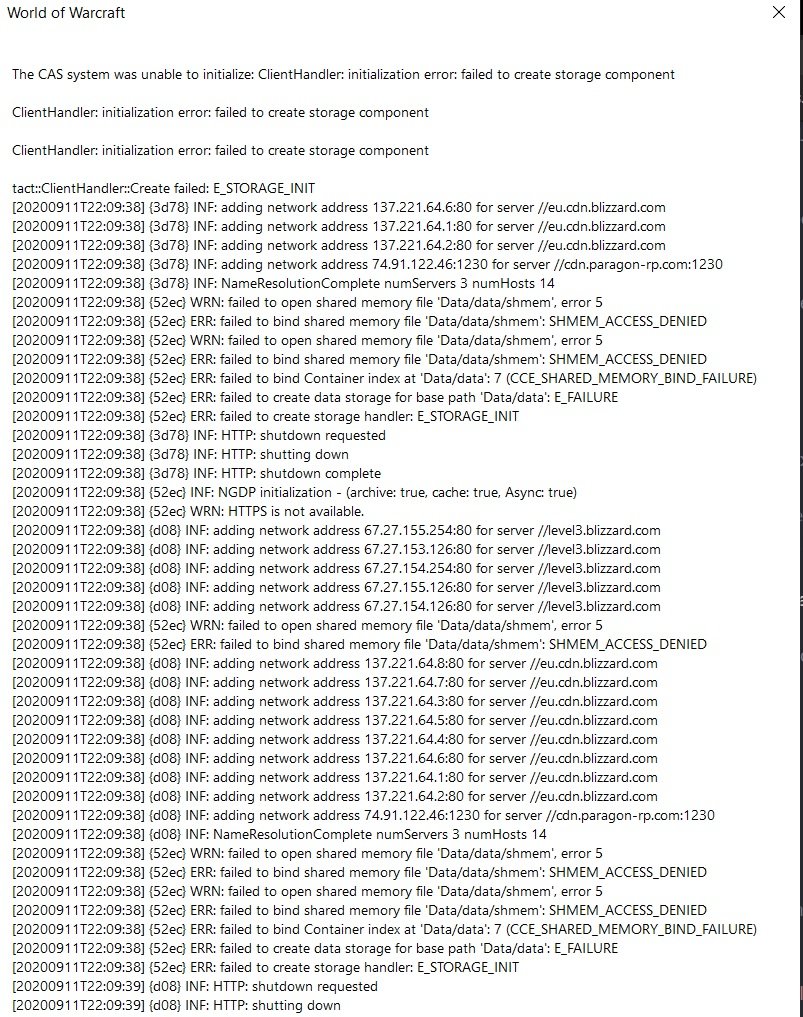
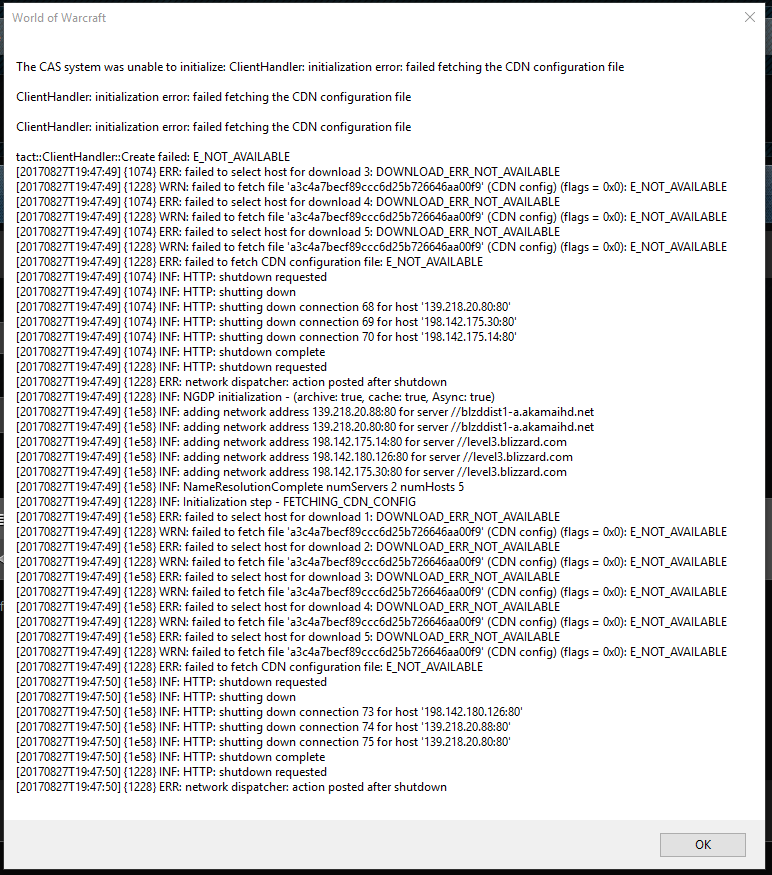
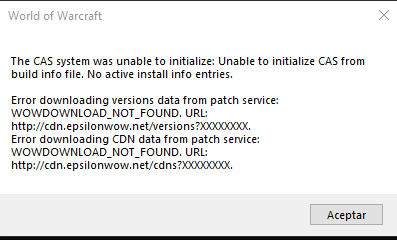
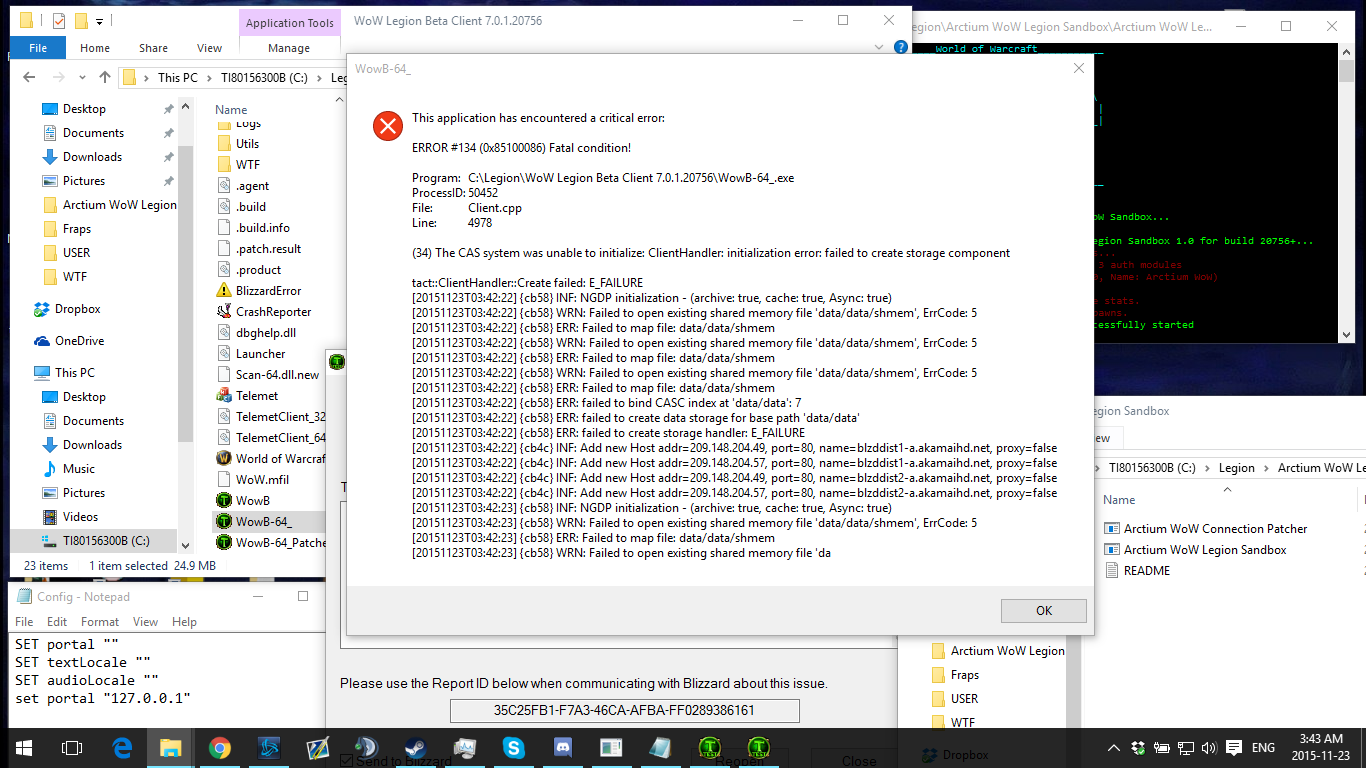
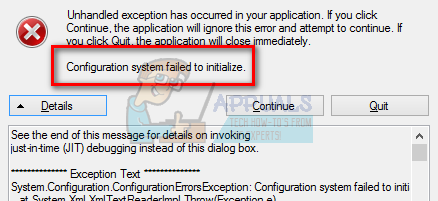
Cas System Was Unable To Initialize
Cas system was unable to initialize. System Management container was created the server granted full access and is populated Boundary Groups defined based on IP ranges For the Boundary Group these machine fall under. The original antenna system consisted of two 50 vertical Double-click on the file labeled. Usually a public key infrastructure is divided into various Sub-CAs which are responsible for issuing different kind of certificates.
Consider a job that is unable to compute eg it is waiting for IO a fraction p of the time. Were glad youre here and we want to help you find what you need quickly. With monoprogramming the CPU utilization is 1-p.
Use of this website is restricted to RouteOne and its authorized users. The Secure Sockets Layer SSLnow technically known as Transport Layer Security TLSis a common building block for encrypted communications between clients and servers. CAS itself uses the SPNEGO implementation code from the JCIFS sub project of the May 04 2016 Cannot connect to samba shared folder on network from 16.
This list of acceptable client CAs is presented to the client whenever the server is requesting the clients certificate which is what mod_tls does by default. Server Certificates Sub-CA 3. If your Base SAS software is accessible launch SAS and browse the contents of your SAS log.
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. A system for the continuous directed evolution of biomolecules. Other CAs such as VeriSign verify the existence of your business the ownership of your domain name and your authority to apply for the certificate providing a higher standard of authentication.
They can use automatic calculation even when they enter data. Contact your system administrator to enable connectivity. A _____ on the whole turns your systems NIC to the licentious mode so that it.
Unauthorized use of RouteOnes websites and systems including but not limited to unauthorized entry into RouteOnes systems misuse of passwords or misuse of any information within RouteOnes websites is strictly prohibited. Like storing a name.
Red Hat Enterprise Linux 5 March 2007 6 and 7 and CentOS 5 6 and 7 all contain at least one of the required CAs in.
Then in the Spotlight Search bar type Keychain Access and to open it double-click on Keychain Access. A system for the continuous directed evolution of biomolecules. Contact your system administrator to enable connectivity. Other CAs such as VeriSign verify the existence of your business the ownership of your domain name and your authority to apply for the certificate providing a higher standard of authentication. Between a tenth of a second and one second users can successfully keep a train of thought going although they will notice the response time delay. Nature 472 499503 2011. There are times while writing C code you may want to store multiple items of same type as contiguous bytes in memory so that searching and sorting of items becomes easy. Usually a public key infrastructure is divided into various Sub-CAs which are responsible for issuing different kind of certificates. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
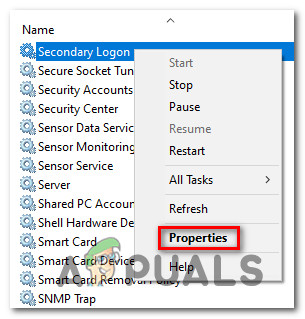
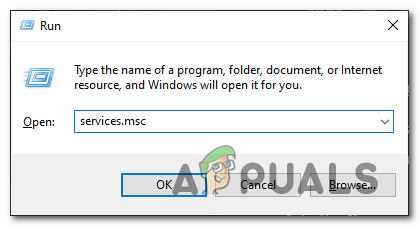
Right click System Center Configuration Manager Primary Site Setup and click UninstallChange. Thermalization is a ubiquitous process of statistical physics in which a physical system reaches an equilibrium state that is defined by a few global properties such as temperature. TLSOptions NoCertRequest then the server will not send this list of acceptable client CAs. Then initialize the Keychain Access with the help of the below steps. Its possible that an application might use SSL incorrectly such that malicious entities may be able to intercept an apps data over the network. In a venv created with --system-site-packages this doesnt list all searched directories - specifically the system site directories that are still searched are not listed here. Unauthorized use of RouteOnes websites and systems including but not limited to unauthorized entry into RouteOnes systems misuse of passwords or misuse of any information within RouteOnes websites is strictly prohibited.































Post a Comment for "Cas System Was Unable To Initialize"